Deploying Zola (part 2) behind a proxy server
Categories: Tech munchies
Tags: zola nginx FreeBSD proxy server
Motivation
When having some web servers running on jails or virtual machines you must have a proxy server to broadcast your requests. Once the syntax of nginx set up is understood, the configuration is a breeze.
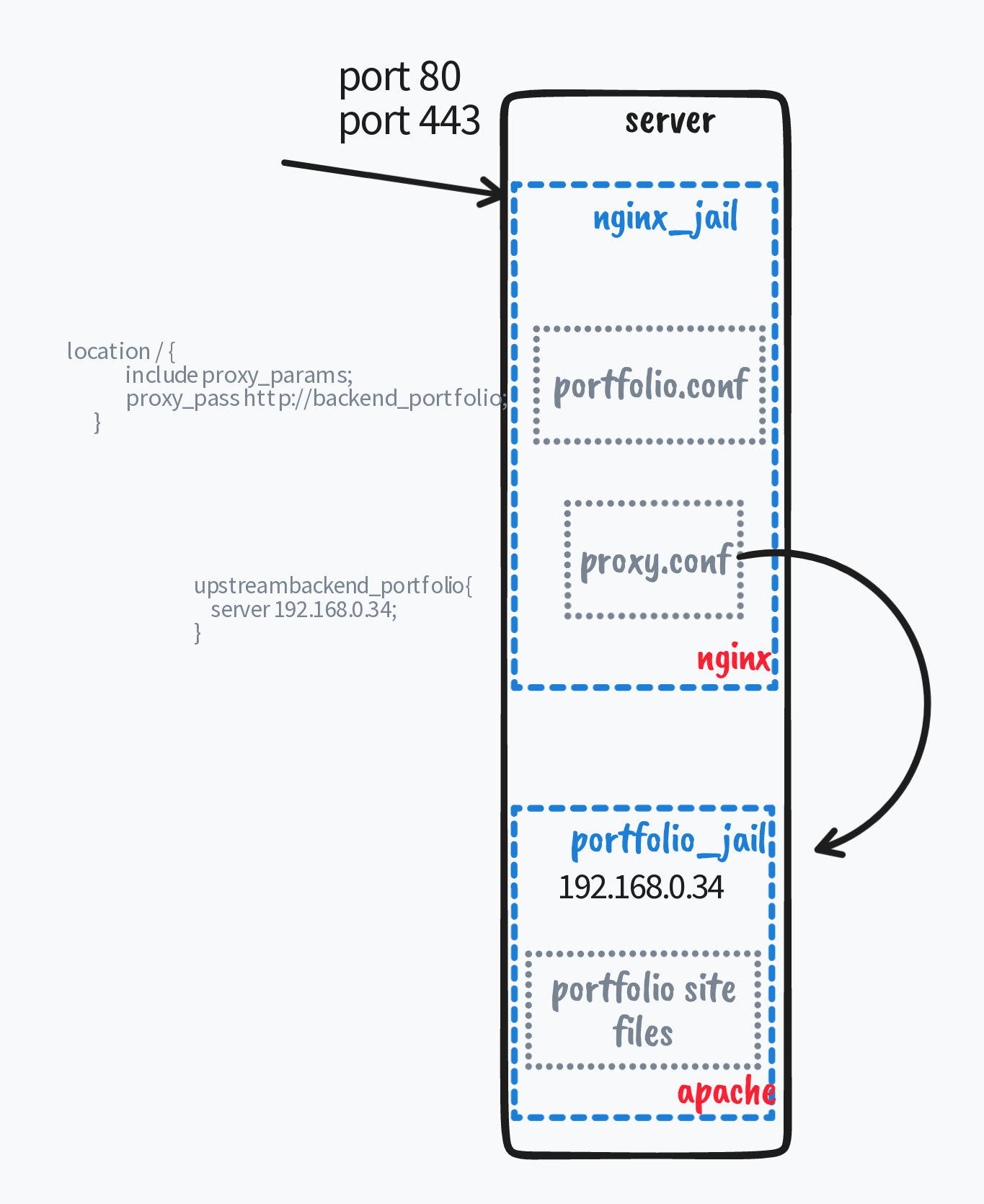
Nginx runs in a jail
A jail is especially dedicated to nginx. Its installation is obvious through the pkgsystem. Then the configuration files remain in `/usr/local/etc/nginx'.
nginx.conf
The main config file is nginx.conf and is left slightly unchanged.
#user nobody;
worker_processes 1;
#error_log /var/log/nginx/error.log;
#pid logs/nginx.pid;
events {
worker_connections 1024;
}
http {
include mime.types;
default_type application/octet-stream;
#
sendfile on;
#tcp_nopush on;
#keepalive_timeout 0;
keepalive_timeout 65;
#gzip on;
#include blockips.conf
include conf.d/*.conf;
include Includes/*;
}
The only the last line points to the Includes/* directory where all the configurations of proxied web sites take place likewise the apache setting in FreeBSD.
Includes/portfolio.conf
/usr/local/etc/nginx/Includes/portfolio.conf
The portfolio site entry in the proxy server is listed above. The variables to document are :
- server_name ;
- access_log ;
- error_log ;
- location ;
- proxy_pass ;
https stuff is already written by Certbot, we only have to document the server_name.
server {
server_name portfolio.osca.dev;
access_log /var/log/nginx/portfolio.osca.dev.log;
error_log /var/log/nginx/portfolio.osca.dev.error.log;
location / {
include proxy_params;
# see *** proxy.conf ****
proxy_pass http://backend_portfolio;
}
#error_page 404 /404.html;
# redirect server error pages to the static page /50x.html
#
error_page 500 502 503 504 /50x.html;
location = /50x.html {
root /usr/local/www/nginx-dist;
}
listen 443 ssl; # managed by Certbot
ssl_certificate /where_the_certbot_stuff_is/fullchain.pem; # managed by Certbot
ssl_certificate_key /where_the_certbot_stuff_is/privkey.pem; # managed by Certbot
include /where_the_certbot_stuff_is/options-ssl-nginx.conf; # managed by Certbot
ssl_dhparam /where_the_certbot_stuff_is/ssl-dhparams.pem; # managed by Certbot
}
server {
if ($host = portfolio.osca.dev) {
return 301 https://$host$request_uri;
} # managed by Certbot
listen 80;
server_name portfolio.osca.dev;
return 404; # managed by Certbot
}
proxy.conf
proxy.confis the file where nginx can find the ip address of the target host the name of the upstream is prefixed by backend_. The entry upstream translates https://backend_portfolio the proxypass variable in portfolio.confinto a local URL. There is where the magic takes place and nginx acts as a proxy server.
/usr/local/etc/nginx/conf.d/proxy.conf
...
upstream backend_xxx{
server 192.168.0.34;
}
upstream backend_portfolio{
server 192.168.0.34;
}
upstream backend_yyy{
server 192.168.0.35;
}
...
Checking and reloading nginx
configtest
root@nginx /u/l/e/nginx# service nginx configtest
Performing sanity check on nginx configuration:
nginx: the configuration file /usr/local/etc/nginx/nginx.conf syntax is ok
nginx: configuration file /usr/local/etc/nginx/nginx.conf test is successful
reload
root@nginx /u/l/e/nginx# service nginx reload
Performing sanity check on nginx configuration:
nginx: the configuration file /usr/local/etc/nginx/nginx.conf syntax is ok
nginx: configuration file /usr/local/etc/nginx/nginx.conf test is successful